Thor ransomware virus removal. New locky new .Thor extension.
Locky is back and turns its attention to new file .Thor extension.
.Thor ransomware decrypt. Ransom note _what_is.
Thor ransomware or .thor extension is part of locky malware. It is considered to be dubbed Thor ransomawre after the extension, however it is Locky virus. A day after a new .shit extension appended to locked files a new locky variant is reported to append .thor extension. What is interesting is that all three extensions .odin, .shit and .thor are in distribution. As previously mentioned Locky si one the biggest names into the ransomware family, along with cerber and a few more. Cerber the winter so far, however Locky may be trying to catch up as it was never been so active in distribution and updates. Upon further inspection, rather than different .odin, .shit and .thor extensions, not much is changed except the distribution tactics. Extensions .shit and .thor comes not long after Locky switches to LNK email file attachments. As the previous variant, Locky will be installed by a DLL executed by Rundll32.exe.
Unfortunately as of this time the only option to restore locked files is from offline backups of pay what locky asks, however paying is highly unrecommended.
First reports of Locky ransomware were in the middle of February 2016, appending .locky extension to encrypted files. All developments of locky are designed what any ransomware is designed to behave. Once computer system is infected, vicitm’s files will be encrypted and depending on the locky variant .odin, .shit or .thor extension appended to locked files. Locky will also present a new type of ransom note left at user desktop ransom note “_what_is.bmp” and “_what_is.html”. The ransom note provide information for victims, regarding payment and how to perform such in order to unlock files. AES encryption algorithm will be responsible for encryption of targeted file after a scan of storage drive and network shares. User background will be also changed with the one of locky ransom note image.
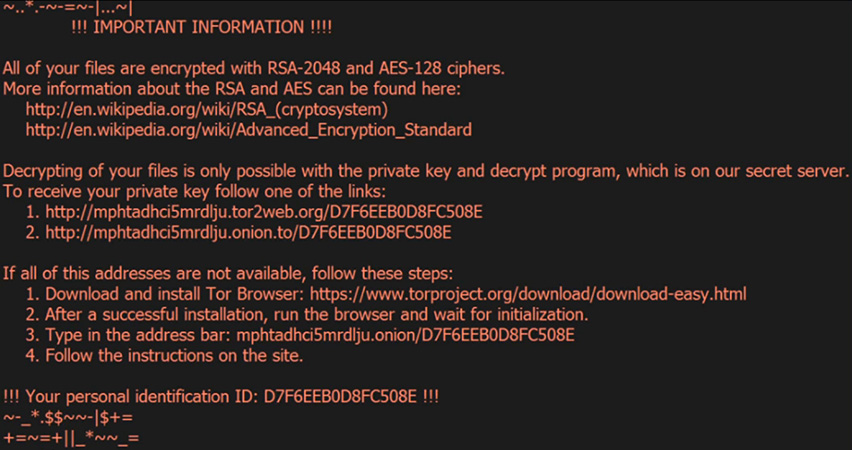
Since first reported locky demands were rather floating. We have seen locky demand 0.3 BTC up to 2 BTC, which is approximately $200 up to $1300. In order to make payment user will have to download and install TOR browser to get access of locky payment panel.
All of the mentioned variants in this post are currently distributed by SPAM emails with malicious HTA, JS, or WSF attachments. Once the virus file attachment executed it will download an encrypted DLL installer, which will be decrypted and executed on a infected computer system. As of this time Locky targets over 380 file extension for encryption.
There is a similar to locky campagne called Bart, which was also currently upgraded. Bart ransomawre payment panel is the same as lcoky, but just with a different name. With Bart ransomware reported, Locy was upgraded switching from .lcoky to .zepto extension back then. Since then Locky no longer connect remote Command & Control server, instead it is using RockLoader to deliver over HTTPS.
Security researchers report that .try extension is soon to be expected. Try can be the next locky extension that will be appende to locked files. It may be also dubbed as Try ransomware after the extension, which aspire to be a common practice now, however it is Locky ransomware.
How to protect against ransomware is most frequently asked questions in the past year. Since ransomware has become the biggest threat among all viruses, people ask themselves if there’s a way to protect from such. It is already too late if you once suffered ransom attack and file has been locked. For some there is a solution but for others disappointment. Either way popularity of ransomware rises and new development are presented every day.
What can we do against the battle with ransomware?
- If you are already infected do not pay the ransom! Remove the virus and look for other solutions rather than paying. Paying the ransom may be your only option if you have really valuable data. However we do not recommend doing this because you will support the work of criminals. The risk of losing money and still stuck with encrypted files since there is no guarantee in any way that you will recover what one is lost.
- Security researcher are always working on recovery solutions. Not all ransomware are professionally developed and being cracked, but some are so good developed that there is no current way to be beaten at the current date. One of the solutions is system restore.
- Best solution is if you have a backup, wipe your hard drive and perform system restore. If not, backup your data frequently. Store backup data in any removable storage device or use any online backup services.
- Protect your computer with antivirus, internet security, anti-malware software or new developed applications like anti-ransomware. Highly recommended is to keep it up to date and use the paid surveys. We do not recommend free applications.
Now that you have been infected you have a few options:
Many suggest that you simply pay and hope that you will get all off your data back. However in this case you risk losing money and still being stuck with crypted files. We do not recommend this way simply because you will support the work of hackers and the more money thay get the stronger they will become.
The best option for you is if you have a backup, wipe your hard drive and perform system restore.
Use any type of anti malware software to remove Thor Ransomware.
NOTE: In this option the virus will be removed but the files will remain locked! You have to decrypt your files.
New research discovery shows how ransomware deletes files and substitute encrypted copy of them. It is not guaranteed, but it is a possibility that you may recover your files with data recovery software. Before trying to decrypt any files you can scan your computer for posible data loss.
Go here to find out how to recover deleted files.
Decrypt Locky Ransomware files with .thor extension.
Good news is that we can now use decryption programs. A lot of security companies like Kasperky lab, bitdefender and more has developed a program that is fully capable of decryption key for ransomware malware. You can find this programs anywhere on the internet but it is strongly suggested to download this programs from official websites. NOTE: It may take a long time for your files to be decrypted depending on your PC performance.
- Name – Thor
- Type Spamming – Malware, Ransomware, Trojan Horse
- Danger Level – High
- Brief Description – Encrypt files and demand ransom.
- Symptoms – Poor pc performance or freezing, ransom massages.
- Method – Via Trojan Horse or spam email.
Note: Removing Thor Ransomware manually could be very risky and unpredictable!
To remove this virus we suggest you follow the step by step instructions we provided. Since ransomware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
No Comments Yet