In the vast digital realm, safeguarding one’s online presence is of paramount importance. As our reliance on the internet intensifies, spanning professional communications to personal leisure, ensuring the security of online interactions is crucial. Google Chrome, a globally dominant web browser, is central to these interactions. Its extensive user base makes it an attractive target for cyber threats. Among these threats, browser hijackers have emerged as particularly insidious, often operating covertly until their detrimental effects become apparent.
What is a browser hijacker?
A browser hijacker is malicious software crafted to modify a user’s browser settings without their knowledge or consent. Within the Google Chrome environment, these modifications can include altering the default homepage, introducing unwanted extensions, or redirecting users to specific, potentially harmful, websites. The primary motives behind such unauthorized changes vary: from generating advertising revenue and redirecting web traffic to more malicious intents like capturing sensitive user data. While they may seem trivial at first glance, the ramifications of browser hijackers are profound, potentially leading to system compromises and data breaches.
Mechanisms of browser hijacking
Browser hijackers, though often underestimated, utilize intricate tactics to breach systems, and Google Chrome is no exception. Their strategies are deeply rooted in deception:
- Bundled software. A prevalent method of infiltration involves software bundling. Users, when downloading software, particularly from third-party sources, may unintentionally install additional undesired programs, including hijackers. These programs often lurk within ‘Advanced’ or ‘Custom’ installation options.
- Deceptive pop-up ads. Some hijackers penetrate systems when users engage with misleading pop-up ads. These ads can imitate genuine system alerts or software update prompts, deceiving users into downloading the hijacker.
- Malicious email attachments. Phishing emails bearing malicious attachments or links can also introduce browser hijackers. Users who inadvertently open these attachments or engage with the links may activate the hijacker.
- Compromised websites. Accessing compromised or malevolent websites can trigger an automatic browser hijacker download. Such sites typically exploit vulnerabilities in outdated browsers or plugins.
- Fake extensions or plugins. Google Chrome’s vast extension ecosystem, while beneficial, can be a double-edged sword. Fake or malicious extensions can function as hijackers. Users might be enticed into installing these, believing they offer valuable features, only to have their browsing experience deteriorate.
Browser hijacking risks
The perils of browser hijacking extend beyond mere disruptions:
- Data Theft. Numerous hijackers are engineered to monitor and harvest user data, encompassing browsing patterns, search queries, and even login credentials. This data can be traded on the dark web or exploited for identity theft.
- Malware Introduction. Hijackers can pave the way for other malicious software, further jeopardizing system security. They might introduce ransomware, trojans, or spyware.
- System performance degradation. A hijacker’s presence can strain system resources, resulting in sluggish performance, recurrent crashes, and diminished battery longevity on mobile devices.
- Misleading information. Hijackers can reroute users to counterfeit websites or present altered search outcomes, subjecting users to deceptive or erroneous information.
- Financial loss. By diverting users to counterfeit e-commerce or banking portals, hijackers can trick users into executing fraudulent transactions or disclosing financial details.
Examples of Google Chrome browser hijackers
Given Google Chrome’s ubiquity across both Mac and Windows platforms, it’s frequently targeted. Here are some prominent examples of browser hijackers that have plagued Chrome users across these operating systems:
Windows:
- GoCouponSearch: This deceptive application offers discount coupons for various online retailers. However, it modifies the browser’s search engine and redirects search queries to display ads and monitor user searches.
- GoSave: Portrayed as a beneficial browser add-on, GoSave promises to showcase special offers and discounts. In reality, it’s intrusive, presenting ads irrespective of user preferences.
- CoolWebSearch: This hijacker infiltrates systems during the download of other freeware or apps. It introduces dubious bookmarks and generates desktop shortcuts, affecting the computer’s overall performance and browser speed.
- RocketTab: Typically bundled with other software, RocketTab introduces multiple browser toolbars, decelerates webpage loading, and bombards users with pop-up ads.
- Ask Toolbar: This search utility is often bundled with other products during their download or installation. It can disrupt keyword searches, redirecting users to Ask.com instead of their chosen search engine. It may also set Ask.com as the default homepage.
Mac:
- Search Marquis: This counterfeit search engine modifies browser settings, especially the “new tab” and “default search” configurations. It reroutes users to an ad-filled custom search page, generating revenue for the perpetrators.
- Search Alpha: Another spurious search engine, Search Alpha redirects users to an ad-saturated custom search page.
- Yahoo redirect virus: This hijacker reroutes users to Yahoo search results, even if it’s not their default search engine. It’s part of a broader category of browser redirect viruses aiming to mislead users and generate ad revenue.
- Bing redirect: Analogous to the Yahoo Redirect Virus, this hijacker redirects users to Bing search results.
- Safe Finder: This browser hijacker alters browser settings to redirect users to its proprietary search engine, typically filled with ads.
How to get rid of browser hijackers on Windows
- Remove unwanted software from your PC: Browser hijackers often infiltrate systems via third-party software or media files from unverified sources. Identify and terminate suspicious apps using the Task Manager. Navigate to the Windows 10/11 Settings menu, select ‘Apps & features‘, and uninstall any unfamiliar or potentially malicious apps.
- Scan for browser hijackers using Windows Security: Malicious files can accompany downloads from unverified sources. While third-party antivirus tools can detect and eliminate these files, Windows Security, an integrated tool, can be equally potent. Press the Windows key, search for Windows Security, select ‘Virus & threat protection‘, and initiate a quick system scan.
- Reset Google Chrome to default settings: Launch Chrome, click on the 3-dot menu, navigate to ‘Settings‘, select ‘Reset settings‘, and click ‘Restore settings to their original defaults‘.
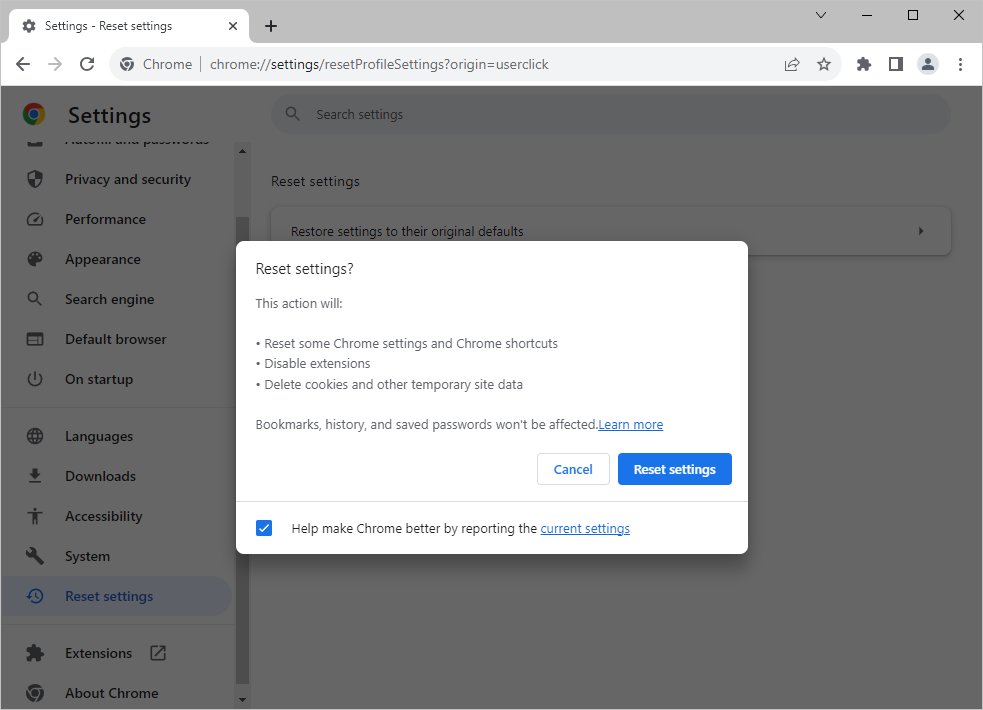
- Remove unknown extensions: Some hijackers function via extensions. Eliminate any irrelevant or suspicious extensions to maintain a pristine browsing experience. Launch Google Chrome, click on the 3-dot menu icon, expand ‘More Tools‘, select ‘Extensions‘, and remove any unfamiliar or superfluous extensions.
How to remove Chrome browser hijackers on macOS
Mac users are not immune to browser hijackers on Google Chrome. Here’s a structured approach to address and remove these hijackers, emphasizing the Search Marquis removal for Chrome:
- Locate and remove malware: Navigate to Apple Menu > About This Mac. Click ‘Overview‘, select ‘System Report‘, expand the ‘Software‘ section, click ‘Applications‘, and organize applications by the most recent modification date in the “Last Modified” column. Uninstall any unfamiliar applications.
- Check CPU usage for suspicious apps: Access the CPU tab and monitor for high CPU usage. If an unfamiliar program emerges, verify its legitimacy online. If deemed malicious, note its location, navigate to the specific folder, and eradicate the malware.
- Reset Google Chrome settings: Open Chrome, click the 3-dot menu button, select Settings, click Advanced in the sidebar, and choose Reset settings. Click the button saying Restore settings to their original defaults and follow further prompts to reset Chrome settings.
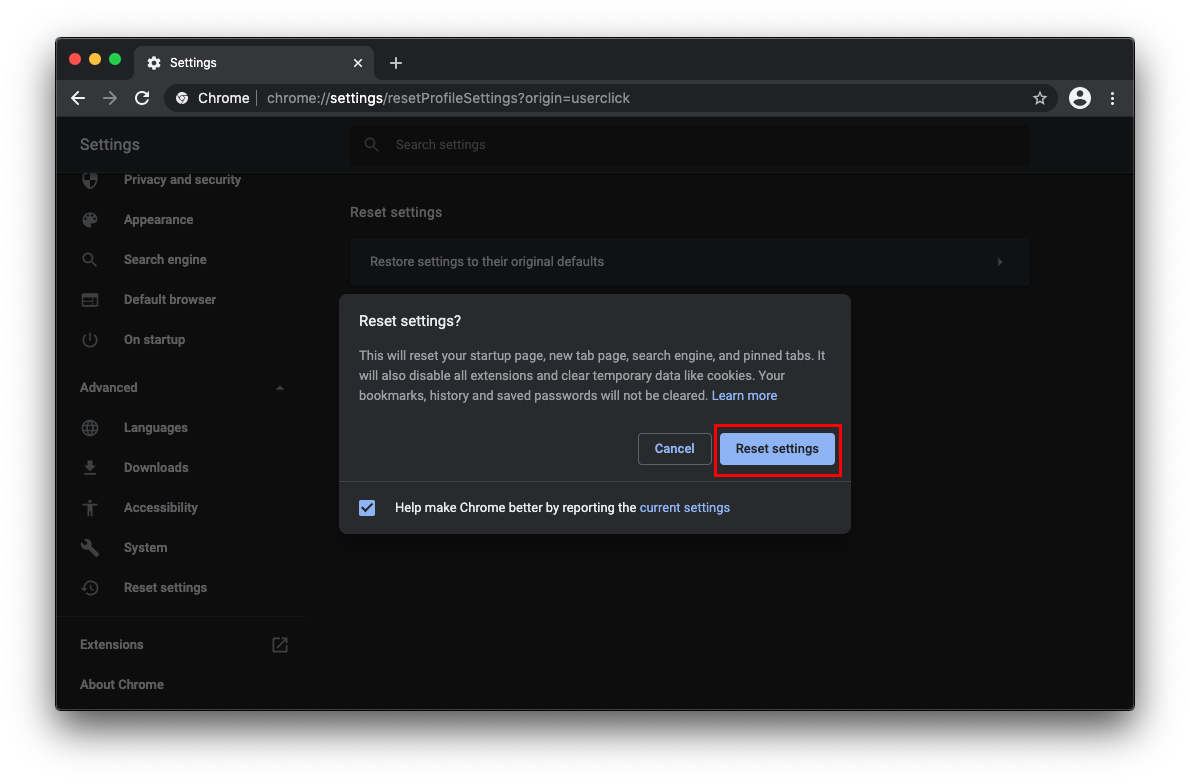
- Choose default search engine: Navigate to 3-dot menu > Settings. In the settings page, locate the ‘Search engine‘ section, manage search engines, remove unwanted search engines, and establish your preferred homepage.
- Uninstall suspicious browser extensions in Chrome: Navigate to Chrome > Preferences > Extensions and eliminate any unfamiliar extensions.
How to Prevent your Google Chrome from Hijacking
1. Regular updates
Ensure your operating system, browser, and other critical software remain current. Developers consistently release updates containing security patches designed to rectify vulnerabilities. Prompt installation of these updates strengthens your system’s defenses against potential hijacking.
2. Avoid suspicious downloads
Exercise caution when downloading software, particularly from free marketplaces or unverified sources. Browser hijackers often use “bundling” to attach themselves to legitimate software downloads. Before downloading, review, verify the source’s authenticity, and choose custom installation to deselect unwanted bundled software.
3. Educate yourself
Knowledge is a formidable tool in cybersecurity. By staying informed about the latest threats, understanding their strategies, and familiarizing yourself with best security practices, you can significantly mitigate the risk of browser hijacking. Regularly consult trusted cybersecurity websites, forums, or news outlets to stay updated on emerging threats and preventive strategies.
4. Use reliable antivirus and anti-Malware software
Invest in reputable antivirus and anti-malware tools. These tools provide real-time protection, scanning downloads and websites for potential threats. They can detect, quarantine, and remove malicious software before it wreaks havoc.
5. Review browser extensions periodically
Periodically assess and audit the extensions installed on your browser. Eliminate any that are obsolete or appear dubious. Hijackers can occasionally pose as seemingly harmless extensions.
6. Be cautious with email attachments and links
Phishing emails can introduce browser hijackers. Always verify the sender’s authenticity before opening any attachments or engaging with links, even if they seem to originate from known contacts.
To recap
Browser hijackers, though frequently overlooked, represent a significant online security threat. By understanding their nature, regularly scanning for them, and knowing how to eliminate them, users can ensure a safer browsing experience on Google Chrome. Whether on a Mac or Windows 10/11 system, maintaining vigilance and proactive cybersecurity practices is essential to thwart browser hijackers.
No Comments Yet