HiddenTear cerber variant dubbed CerberTear ransomware appending .cerber extension.
Ransom note HOW_TO_RESTORE_YOUR_DATA.HTML
CerberTear ransomware is a HiddenTear cerber variant reported to append .cerber extension. It’s called CerberTear Ransomware after the extension .cerber, which is well known and HiddenTear development, what seems to be a combination of two vary famous developments. However there is no relation between cerber and HiddenTear ransomware.
ATTENTION!!!
Since malware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
>>Click here to download free anti-malware removal tool.<<
Hackers are constantly creating new ways to infect user system. In this case after the infection is done the virus starts to encrypt your files. That means that once files locked, they will be unable to open or lose functionality. This is achieved thanks to special encrypting algorythms, that can be decrypted only by a generated RSA key, stored in the command and control server. In all ransomware variants this key is provided in return of a payment, mostly in bitcoins. Our advice is to avoid paying anything to the cyber-criminals before you seek help from IT specialist.
It is a common practice to name the virus after the appended extension, but this is not always correct. In most cases victims have no idea about the nature of the ransomware, so they take the name from the ransom note or from the appendix. However in this case we have something totally new. A .cerber extension appnded but a HiddenTear ransomware attack. Extension, which will confus a lot of victims, searching for cerber ransomware and what they will find is something totally different from what they are trying to find. Infected user must be aware for ransomware viruses, because they can cause loss of valuable data.
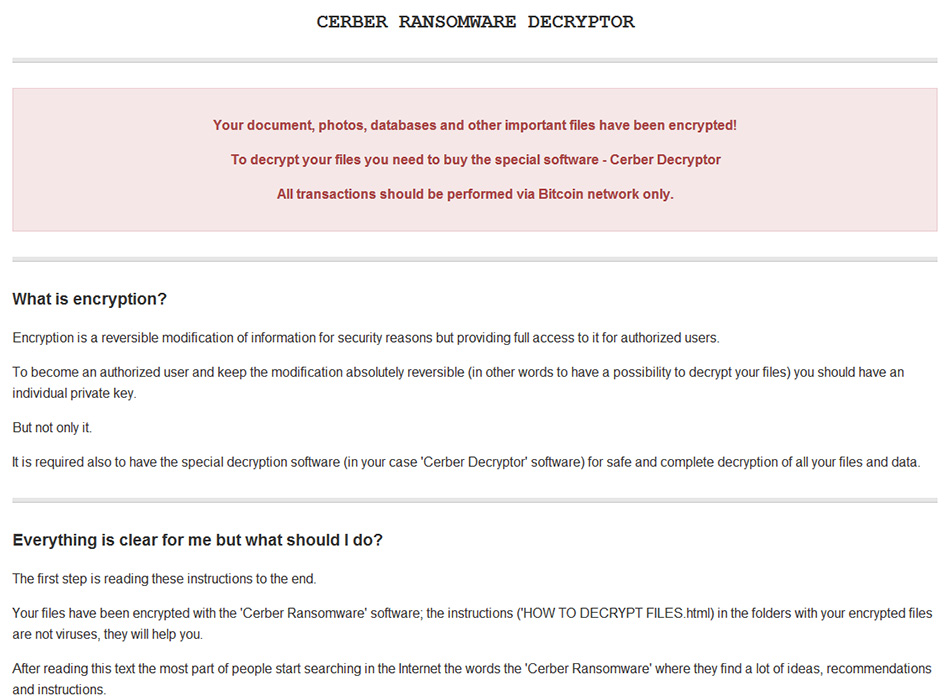
The confusion is even bigger when victims open the ransom note HOW_TO_RESTORE_YOUR_DATA.HTML left at desktop, which also use the cerber name. However claiming to be cerber ransomware does not mean it is that good in development. Unlike cerber this ransomware development may be crackable.
Anyway CerberTear has all distinguishable features of a ransomware. It seeks for weak spots in the protection of your system and infiltrates the PC. After the infection the ransomware encrypts your file with the addition of an extension .cerber. For example a .jpg files becomes .jpg.cerber, .pdf files .pdf.cerber and etc. It will also show you a ransom note HOW_TO_RESTORE_YOUR_DATA.HTML with information about restore and payment options. All victims should try restoring from other solutions rather than paying.
Unfortunately as the ransomware is still new there is no free solution. Security researchers are working on a decryption tool developing so it is a matter of time until Cerber Tear ransomware may be cracked.
ATTENTION!!!
Since malware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
>>Click here to download free anti-malware removal tool.<<
How to protect against ransomware is most frequently asked questions in the past year. Since ransomware has become the biggest threat among all viruses, people ask themselves if there’s a way to protect from such. It is already too late if you once suffered ransom attack and file has been locked. For some there is a solution but for others disappointment. Either way popularity of ransomware rises and new development are presented every day.
In general there are three types of ransomware reported as of this time.
- Lockscreen ransomware – Rather than encrypting files, this type of ransomware will display full-screen message that prevents user from accessing the system. In order to restore access the ransomware will ask user to pay a fee.
- Encryption ransomware – This type of ransomware will encrypt files. Encrypted files will be locked and user will no longer able to open them. The ransomware developer will ask user to pey in order to unlock, decrypt files.
- MBR locker ransomware – This ransomware will rewrite Master Boot Record and prevents user from accessing the system. After a reboot a message will ask users to pay a ransom to unlock PC.
What can we do against the battle with ransomware?
- If you are already infected do not pay the ransom! Remove the virus and look for other solutions rather than paying. Paying the ransom may be your only option if you have really valuable data. However we do not recommend doing this because you will support the work of criminals. The risk of losing money and still stuck with encrypted files since there is no guarantee in any way that you will recover what one is lost.
- Security researcher are always working on recovery solutions. Not all ransomware are professionally developed and being cracked, but some are so good developed that there is no current way to be beaten at the current date. One of the solutions is system restore.
- Best solution is if you have a backup, wipe your hard drive and perform system restore. If not, backup your data frequently. Store backup data in any removable storage device or use any online backup services.
- Protect your computer with antivirus, internet security, anti-malware software or new developed applications like anti-ransomware. Highly recommended is to keep it up to date and use the paid surveys. We do not recommend free applications.
Now that you have been infected you have a few options:
Many suggest that you simply pay and hope that you will get all off your data back. However in this case you risk losing money and still being stuck with crypted files. We do not recommend this way simply because you will support the work of hackers and the more money thay get the stronger they will become.
The best option for you is if you have a backup, wipe your hard drive and perform system restore.
Use any type of anti malware software to remove CerberTear ransomware.
NOTE: In this option the virus will be removed but the files will remain locked! You have to decrypt your files.
New research discovery shows how ransomware deletes files and substitute encrypted copy of them. It is not guaranteed, but it is a possibility that you may recover your files with data recovery software. Before trying to decrypt any files you can scan your computer for posible data loss.
Go here to find out how to recover deleted files.
Decrypt CerberTear ransomware files with .cerber extension.
Good news is that we can now use decryption programs. A lot of security companies like Kasperky lab, bitdefender and more has developed a program that is fully capable of decryption key for ransomware malware. You can find this programs anywhere on the internet but it is strongly suggested to download this programs from official websites. NOTE: It may take a long time for your files to be decrypted depending on your PC performance.
- Name – CerberTear
- Type Spamming – Malware, Ransomware, Trojan Horse
- Danger Level – High
- Brief Description – Encrypt files and demand ransom.
- Symptoms – Poor pc performance or freezing, ransom massages.
- Method – Via Trojan Horse or spam email.
Note: Removing CerberTear ransomware manually could be very risky and unpredictable!
To remove this virus we suggest you follow the step by step instructions we provided. Since ransomware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
No Comments Yet