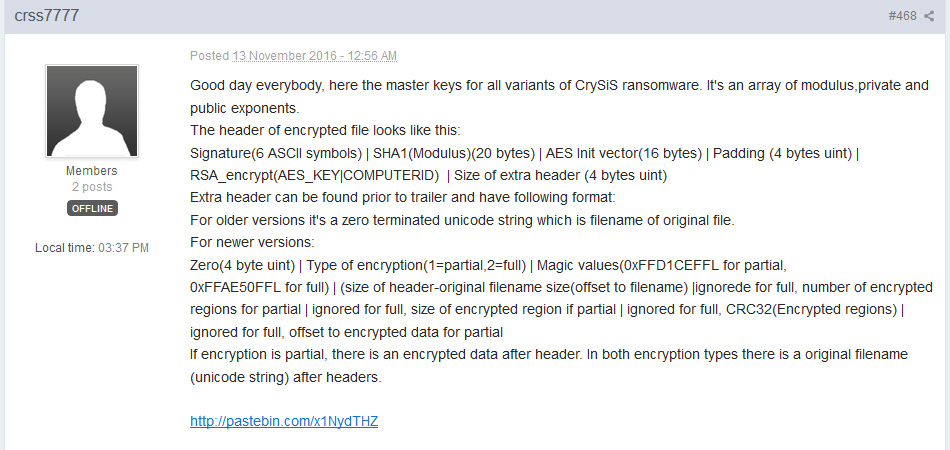
CrySis ransomware master key published.
Security researchers working on a decryption tool.
CrySis ransomware master key reported to be published just recently by security researchers, which are working on a decryption tool. This a great news for victims suffered from CrySis rasnomware and .xtbl extension appended to locked files. Is this the end of CrySis projekt or developers are working on a new ransom development, which may be better or worst it is not know as of yet. However victims can be confident that CrySis will soon be in history of ransomware and working decryption tool, which will unlock encrypted files by CrySis.
ATTENTION!!!
Since malware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
>>Click here to download free anti-malware removal tool.<<
CrySis rasnomware master key release is not the first closed project. Teslacrypt project was also shut down not long ago releasing master key for victims to recover from it. However developer moved to a bigger Cryptxxx campane, making a lot of new and very good ransomware developments. Is CrySis rasnomware master key announcement the next step of a new ransomware like what happened with Teslacrypt project is soon be discovered.
CrySis rasnomware master key should unlock all variants, which were a lot over the past few months. Since CrySis was reported it was a big name into the ransomware family, releasing variety of development most named after the contact email left and .xtbl extension. At the beginning not much of credit was given to CrySis development, however not long after it was reported a big increase of infected users was spotted by security researchers. With the rise of CrySis era, variety of versions were constantly reported. This was really a nasty ransomware, which targeted more than 185 file types, including documents, executables, media, spread sheets PDFs (For full list of targeted extensions for encryption see below). The latest reported and may be the last variant was Nomoneynohoney@india.com. CrySiS itself started to spread in February 2016 reaching its peak in popularity surpassing established ransomware like Locky.
Many of the CrySiS developments were including many intresting features, bringing individually to its kind, however CrySiS is no more. As most good ransomware developments, algorithms used to encrypt users data was a combination of RSA and AES, also deleting the system’s shadow copies, which is backup copies or snapshots of computer files or volumes. The .xtbl extension appende was well know along with email before it. Stay toon for a decryption tool announcement, which can be found at no more ransomware project
How to protect against ransomware is most frequently asked questions in the past year. Since ransomware has become the biggest threat among all viruses, people ask themselves if there’s a way to protect from such. It is already too late if you once suffered ransom attack and file has been locked. For some there is a solution but for others disappointment. Either way popularity of ransomware rises and new development are presented every day.
In general there are three types of ransomware reported as of this time.
- Lockscreen ransomware – Rather than encrypting files, this type of ransomware will display full-screen message that prevents user from accessing the system. In order to restore access the ransomware will ask user to pay a fee.
- Encryption ransomware – This type of ransomware will encrypt files. Encrypted files will be locked and user will no longer able to open them. The ransomware developer will ask user to pey in order to unlock, decrypt files.
- MBR locker ransomware – This ransomware will rewrite Master Boot Record and prevents user from accessing the system. After a reboot a message will ask users to pay a ransom to unlock PC.
What can we do against the battle with ransomware?
- If you are already infected do not pay the ransom! Remove the virus and look for other solutions rather than paying. Paying the ransom may be your only option if you have really valuable data. However we do not recommend doing this because you will support the work of criminals. The risk of losing money and still stuck with encrypted files since there is no guarantee in any way that you will recover what one is lost.
- Security researcher are always working on recovery solutions. Not all ransomware are professionally developed and being cracked, but some are so good developed that there is no current way to be beaten at the current date. One of the solutions is system restore.
- Best solution is if you have a backup, wipe your hard drive and perform system restore. If not, backup your data frequently. Store backup data in any removable storage device or use any online backup services.
- Protect your computer with antivirus, internet security, anti-malware software or new developed applications like anti-ransomware. Highly recommended is to keep it up to date and use the paid surveys. We do not recommend free applications.
Now that you have been infected you have a few options:
Many suggest that you simply pay and hope that you will get all off your data back. However in this case you risk losing money and still being stuck with crypted files. We do not recommend this way simply because you will support the work of hackers and the more money thay get the stronger they will become.
ATTENTION!!!
Since malware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
>>Click here to download free anti-malware removal tool.<<
The best option for you is if you have a backup, wipe your hard drive and perform system restore.
Use any type of anti malware software to remove CrySis ransomware
NOTE: In this option the virus will be removed but the files will remain locked! You have to decrypt your files.
New research discovery shows how ransomware deletes files and substitute encrypted copy of them. It is not guaranteed, but it is a possibility that you may recover your files with data recovery software. Before trying to decrypt any files you can scan your computer for posible data loss.
Go here to find out how to recover deleted files.
Decrypt CrySis ransomware files with .xtbl extension.
Good news is that we can now use decryption programs. A lot of security companies like Kasperky lab, bitdefender and more has developed a program that is fully capable of decryption key for ransomware malware. You can find this programs anywhere on the internet but it is strongly suggested to download this programs from official websites. NOTE: It may take a long time for your files to be decrypted depending on your PC performance.
- Name – CrySis
- Type Spamming – Malware, Ransomware, Trojan Horse
- Danger Level – High
- Brief Description – Encrypt files and demand ransom.
- Symptoms – Poor pc performance or freezing, ransom massages.
- Method – Via Trojan Horse or spam email.
Note: Removing CrySis ransomware manually could be very risky and unpredictable!
To remove this virus we suggest you follow the step by step instructions we provided. Since ransomware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
No Comments Yet