Cerber ransomware back to zero. Note _README_.hta.
Since first reported cerber is one of the best ever developed as of this time ransomware. For the past few months cerber authors have introduced a new variants every single month beginning with .cerber2 extension to .cerber3 and variant with ransom 4char extension along with a new README.hta note. First reports regarding cerber attack were at the beginning of 2016. Since then cerber ransomware is considered to be the biggest names in this industry, along with few more like locky.
The first Cerber variant was attacking victims over the past few months with a constant flow and .cerber extension appended to encrypted files. Many attempts were made by security researchers to crack the virus and develop free decryption tool, many unsuccessful. However Cerber was left with no upgrades way too long, which led to cracking it and checkpoint was able to develop a working decryption tool. Yes good news but not for long. Cerber developers rushed in fixing the problem and came with an updated version, which was appending .cerber2 extension. Now we see a constant change of extension as .cerber3 was reported not long after .cerber2.
The Most Significant Change were with cerber2 variant, which using Microsoft API CryptGenRandom to generate the key and encrypt files. No matter which variant will be the one to infect user computer system, it will do what ransomware is designed to do. It will encrypt user data, lock victim’s files and demand a ransom in return of decryption. Unfotunatly as of this time, there is no solution for victims already infected with this virus and no way to decrypt files for free. The only way to recover is from buckups or to pay the ransom fee, which is highly unrecommended. It is reported that cerber payment service works ok, however there is always a chance of something going wrong. If necessary to perform ransom payment proceed with conscience.
It is unpredictable what the next step of cerber will be, as it was expected that cerber will follow the updates with numbers after the name cerber as: .cerber2 and .cerber3. However the next variant came unexpected. Instead of .cerber4 developers mix things up with a random 4char extension appended to locked files along with a new ransom note “README.hta”. This was the fifth reported cerber variant, however not all are in distribution. Variants appending .cerber and .cerber2 extensions are back in history now, as .cerber3 and the variant which append random 4char extension and note “README.hta” took over with the biggest ransom campaign ever reported.
A brief description of Cerber3 ransomawre: There are two cerber3 variants reported. No surprise is that this variants will lock victim’s files when executed. Once that done a ransom note #HELP DECRYPT#.txt, “# HELP DECRYPT #.html” and “# HELP DECRYPT #.url” and for the latest cerber3 variant “@___README___@.txt” will be left to user desktop. Bout are in distribution as of this time. The ransom note also appears to be very long.
Some of the contents left by the ransom note #HELP DECRYPT#.txt file.
C_E_R_B_E_R R_A_N_S_O_M_W_A_R_E
#############################################################
C_E_R_B_E_R_R_A_N_S_O_M_W_A_R_E
Cannot you find the files you need?
Is the content of the files that you looked for not readable???
It is normal because the files’ names, as well as the data in your files
have been encrypted.
Great!
You have turned to be a part of a big community “#Cerb3r Ransomware”.
Cerber ransomware with random extension note:
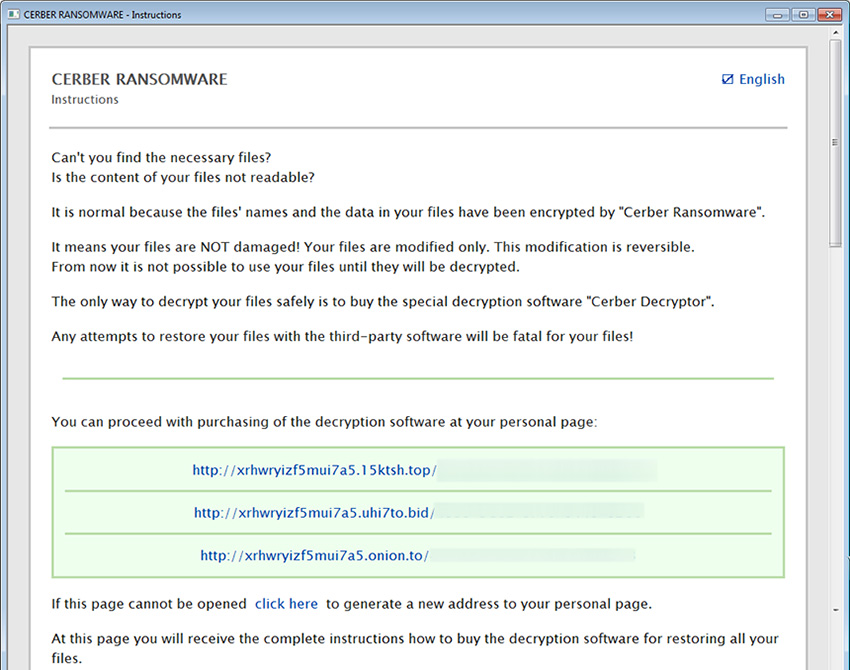
CERBER RANSOMWARE
Instructions
Can’t you find the necessary files?
Is the content of your files not readable?
It is normal because the file’s names and data in your files have been encrypted by “Cerber Ransomware:.
It means your diles are NOT damaged! Your files are modified only. This modification is reversible.
From now it is not possible to use your files until thay will be decrypted.
The only way to decrypt your diles safely is to buy the special decryption software “Cerber Decryptor”.
Any attempts to restore your files with the thied-party sofware will be fatal for your files!
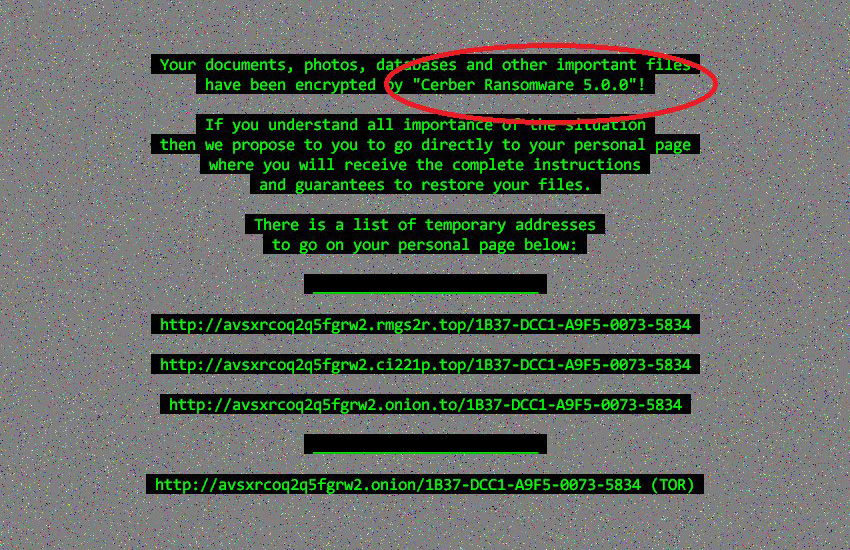
Cerber ransomware appending ransom extension background is also modified to the following image:
Cerber ransomware 5.0.0 came out in less than a day after 4.1.6 version reported. It appears that Cerber is continuing the work behind updating already an uncrackable development, introducing cerber 5.0.0 and cerber 4.1.6 one after another in a day. Bout developments are currently in distribution along with cerber ransomware 4.1.6 which was reported a day before. Users should be aware of malicious Word documents attachments, which will download and install cerber ransomware if opened. Security researchers also report that cerber is using multiple ip addresses to send information to Command & Control servers about infected victims. Something that was not seen in previous cerber variants.
The malicious attachment is pretending to be a invoice with random numbers looking like this: 65849825632.doc. Opening the .doc file will not harm a computer system files, however a massage “Macros have been disabled” and a option to “Enable content”. Once user click on “Enable content” button, winx64.exe will be downloaded from a remote site, saved at %AppData%\winx64.exe and executed. If user is not protected by any some anti-malware tool the virus will begin encrypting user files. It is well know what cerber does once the process of encrypting finish. Encrypted files will have random 4char extension appended, substitute background image and ransom note README.hta will be alos left at user desktop. Once that done the virus will remove itself leaving no trace for antivirus or anti-malware tools.
Cerber ransomware went through many new updates and constant work, which kept it as one of the best developed rasom along with a few more like Locky ransomware. Security researchers form checkpoint successfully developed a working cerber decryption tool unlocking .cerber and .cerber2 extensions for free, however the happiness was not for long. Cerber developers managed to block free decryption option leaving victims with the only choice to pay, however paying highly unrecommended. Cerber payment service is reported to work as it should be, but there is always a chance that something can go wrong. What is to be expected from cerber developers it is unpredictable. They may be go back to .cerber or keep appending random 4char extension we don’t know. What we suspect is that cerber will continue popping up new variants. And yes, not log after Cerber ransomware 5.0.1 was reported.
Cerber ransomware changes faces again and goes to zero days. The last reported variant before this update was cerber ransomware 5.0.1. The new facelift cerber goes back to no numbers and append random random 4char extension. Is this the end of cerber numbering updates and what will be the next step? Who knows?
How to protect against ransomware is most frequently asked questions in the past year. Since ransomware has become the biggest threat among all viruses, people ask themselves if there’s a way to protect from such. It is already too late if you once suffered ransom attack and file has been locked. For some there is a solution but for others disappointment. Either way popularity of ransomware rises and new development are presented every day.
In general there are three types of ransomware reported as of this time.
- Lockscreen ransomware – Rather than encrypting files, this type of ransomware will display full-screen message that prevents user from accessing the system. In order to restore access the ransomware will ask user to pay a fee.
- Encryption ransomware – This type of ransomware will encrypt files. Encrypted files will be locked and user will no longer able to open them. The ransomware developer will ask user to pey in order to unlock, decrypt files.
- MBR locker ransomware – This ransomware will rewrite Master Boot Record and prevents user from accessing the system. After a reboot a message will ask users to pay a ransom to unlock PC.
What can we do against the battle with ransomware?
- If you are already infected do not pay the ransom! Remove the virus and look for other solutions rather than paying. Paying the ransom may be your only option if you have really valuable data. However we do not recommend doing this because you will support the work of criminals. The risk of losing money and still stuck with encrypted files since there is no guarantee in any way that you will recover what one is lost.
- Security researcher are always working on recovery solutions. Not all ransomware are professionally developed and being cracked, but some are so good developed that there is no current way to be beaten at the current date. One of the solutions is system restore.
- Best solution is if you have a backup, wipe your hard drive and perform system restore. If not, backup your data frequently. Store backup data in any removable storage device or use any online backup services.
- Protect your computer with antivirus, internet security, anti-malware software or new developed applications like anti-ransomware. Highly recommended is to keep it up to date and use the paid surveys. We do not recommend free applications.
Now that you have been infected you have a few options:
Many suggest that you simply pay and hope that you will get all off your data back. However in this case you risk losing money and still being stuck with crypted files. We do not recommend this way simply because you will support the work of hackers and the more money thay get the stronger they will become.
The best option for you is if you have a backup, wipe your hard drive and perform system restore.
Use any type of anti malware software to remove Joker_lucker@aol.com.wallet ransomware.
NOTE: In this option the virus will be removed but the files will remain locked! You have to decrypt your files.
New research discovery shows how ransomware deletes files and substitute encrypted copy of them. It is not guaranteed, but it is a possibility that you may recover your files with data recovery software. Before trying to decrypt any files you can scan your computer for posible data loss.
Go here to find out how to recover deleted files.
Decrypt Joker_lucker@aol.com ransomware files with .wallet extension.
Good news is that we can now use decryption programs. A lot of security companies like Kasperky lab, bitdefender and more has developed a program that is fully capable of decryption key for ransomware malware. You can find this programs anywhere on the internet but it is strongly suggested to download this programs from official websites. NOTE: It may take a long time for your files to be decrypted depending on your PC performance.
- Name – Joker_lucker@aol.com.wallet
- Type Spamming – Malware, Ransomware, Trojan Horse
- Danger Level – High
- Brief Description – Encrypt files and demand ransom.
- Symptoms – Poor pc performance or freezing, ransom massages.
- Method – Via Trojan Horse or spam email.
Note: Removing Joker_lucker@aol.com.wallet ransomware manually could be very risky and unpredictable!
To remove this virus we suggest you follow the step by step instructions we provided. Since ransomware virus creates variety of malicious modified registry entries and different files, we strongly advise you to use anti-malware tool. Removing the virus manually requires high computer skills and knowledge.
No Comments Yet